· cybersecurity · 8 min read
What Is Independent Verification and Validation (IV&V)?
With a 239% surge in large breaches (reported to HHS, Office for Civil Rights) involving hacking over the past four years and healthcare data breaches, the stakes for technology in healthcare are at an all-time high. The average costs of a studied breach in healthcare reached nearly $11 million in 2023 – a 53% price increase since 2020.

With a 239% surge[1] in large breaches (reported to HHS, Office for Civil Rights) involving hacking over the past four years and healthcare data breaches, the stakes for technology in healthcare are at an all-time high. The average costs of a studied breach in healthcare[2] reached nearly $11 million in 2023 – a 53% price increase since 2020. Cybercriminals have started making stolen data more accessible to downstream victims, according to the 2023 X-Force Threat Intelligence Report[3].
The sharp increase in large-scale healthcare data breaches, combined with the escalating costs of these incidents, highlights the urgent need for robust Independent Verification and Validation (IV&V) services. With breaches now averaging nearly $11 million each and cybercriminals increasingly targeting healthcare data, organizations must ensure that their technology solutions are not only compliant but also resilient against evolving threats. Implementing comprehensive IV&V processes is critical to proactively identifying vulnerabilities and ensuring that security measures are effectively safeguarding sensitive patient data, ultimately protecting both the organization’s reputation and its bottom line.
Independent Verification and Validation (IV&V) is a critical safeguard in this high-risk environment. By providing an impartial assessment of systems and devices, IV&V helps ensure compliance with stringent safety standards and regulatory requirements.
What Are IV&V Services?
Independent Verification and Validation (IV&V) services involve a comprehensive review, analysis, and testing of software and/or hardware by an objective third party[4]. These services confirm that the system’s requirements are correctly defined (verification) and that the system accurately implements the required functionality and security requirements (validation). Unlike internal testing, IV&V offers an unbiased evaluation, which is important in healthcare and other regulatory industries where strict compliance with safety standards is essential. Employing IV&V enhances[5] the safety, reliability, and regulatory compliance of healthcare technologies by identifying and mitigating potential issues before a product’s launch.
Verification in IV&V
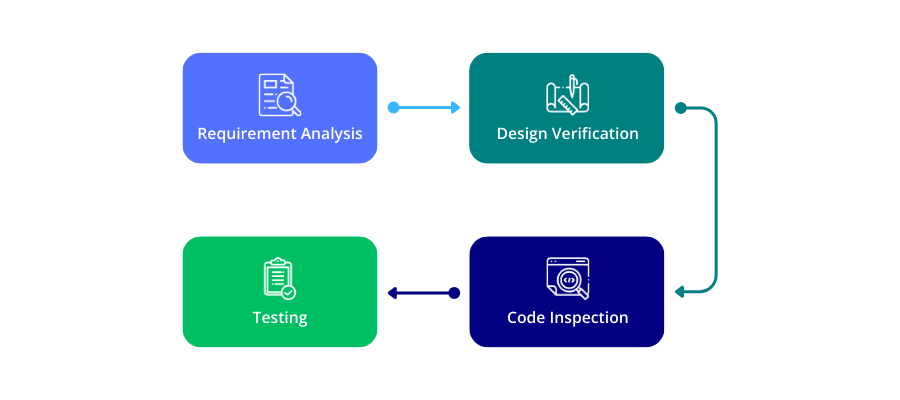
It is a quality control technique focused on assessing whether the system or its components meet defined requirements. During verification, the IV&V team rigorously reviews and examines project processes to prevent omissions, identify problems, and ensure accurate development.
Verification activities may encompass:
- Requirement Verification: ensuring requirements align with defined specifications
- Design Verification: Confirming the design adheres to specified standards
- Code Verification: Validating product code against established standards
- Contract Verification: Checking terms, conditions, and payment against contractual agreements
Techniques employed in verification can include static testing methods, such as:
- Code reviews: systematic examination of source code
- Inspections: peer reviews of work products and documentation
- Walkthroughs: inspecting source code by following logical paths and conditions
These methods focus on the proper use of syntax and adherence to standards, ensuring that every aspect of the project’s product is developed correctly.
Validation in IV&V
This process establishes documented evidence to ensure that a product, service, or system meets its intended requirements and fulfills user expectations.
Validation involves confirming that:
- Requirements: Are clearly defined and accurately reflected
- Designs and Functionality: Conform to the established requirements
- Data Handling: Is correct and appropriate
- Test Results: Are precise and reliable
Techniques used in validation often include dynamic testing approaches, which evaluate the product’s physical response to varying conditions. Key phases of dynamic testing might include:
- Unit Testing: Confirms that individual units of the product function as designed
- Integration Testing: Tests combined units of the product as a group
- Function Testing: Validates that the product’s functionality meets defined requirements
- System Testing: Assesses both hardware and software within an integrated system
- User Acceptance Testing: Performs black-box testing of product functionality to ensure it meets user expectations before release
These dynamic tests help ensure that the final product performs as intended and aligns with user needs.
The Role of IV&V in Healthcare and Medical Devices
IV&V helps in mitigating the risks[6] associated with cybersecurity breaches in healthcare. By providing an independent assessment of the security measures implemented in healthcare systems and medical devices, IV&V ensures that these solutions meet stringent regulatory requirements and industry standards. This process helps identify vulnerabilities before they can be exploited by cybercriminals, thereby safeguarding sensitive patient data and protecting the operational integrity of healthcare organizations.
IV&V depends on two critical processes: verification and validation. Verification and Validation (V&V) are important in healthcare and medical device sectors[7] for improving usability and reliability, reducing failure rates and recalls, and mitigating risks to both patients and users. Despite the availability of guidance on V&V in multiple standards within the medical device domain, manufacturers often find these guidelines challenging to implement due to the lack of consolidated information on successfully achieving them. Independent Verification and Validation (IV&V) steps in to bridge this gap, providing a structured and objective approach that ensures these critical activities are not only executed effectively but also lead to safer and more reliable medical products.
Implementing Independent Verification and Validation (IV&V) services offers several key benefits that enhance the overall quality and success of software development projects in healthcare industry:
- Quality and Process Improvement: IV&V introduces checklists, templates, and tools that enforce a controlled development process, leading to higher-quality outcomes. By providing an objective engineering analysis, IV&V can detect errors[8] that might be overlooked by those closely involved with the project.
- Early Detection of Design Errors: Addressing design errors early in the development process can significantly reduce costs and prevent major consequences that may affect patient outcomes. IV&V helps identify defects and ambiguities in requirements from the outset, minimizing the risk of failures[5] that could negatively impact patient health, company finances, and reputation.
- Lower Management Time Commitment: IV&V offers management enhanced visibility into project progress and quality through objective assessments. By using proven tools and techniques, IV&V can uncover risks and provide strategies for mitigation[6], reducing the time and effort required from management.
- Reduced Overall Cost: Committing to IV&V ensures that the right product is built correctly for patients, reducing the likelihood of delays, field failures, and poor market acceptance. Early error detection and process improvements not only lower immediate costs but also create potential savings for future product developments and extensions.
Key takeaways
In healthcare, where compliance is the biggest risk[9], independent verification and validation (IV&V) is a necessity, not an option. The potential risks of undetected software flaws extend beyond regulatory consequences—they directly impact patient safety[10] and your product’s credibility. Relying solely on internal assessments can leave gaps that only an independent perspective can uncover. Opsfolio’s cybersecurity solution with integrated IV&V services provide not only a machine attestation- and evidence-based cybersecurity tool but also an unbiased evaluation through IV&V, ensuring your healthcare software and devices meet the highest standards of safety and effectiveness which is compliant as well as secured. We help you identify and address issues early, reducing the risk of costly recalls and ensuring your products are ready for the market with confidence.
Bibliography
1. “HHS’ Office for Civil Rights Settles Ransomware Cyber-Attack Investigation,” U.S. Department of Health and Human Services (HHS), October 31, 2023
2. “IBM Report: Half of Breached Organizations Unwilling to Increase Security Spend Despite Soaring Breach Costs,” IBM, July 24, 2023
3. “IBM X-Force Threat Intelligence Index 2024,” IBM, 2024
4. “Independent verification & validation (IV&V),” National Institute of Standards and Technology (NIST), 2024
5. Wallace, Ippolito, and Cuthill, “Reference Information for the Software Verification and Validation Process,” National Institute of Standards and Technology (NIST), April 1996
6. Akella, Rao, and Siddhartha, “Effective Independent Quality Assessment using IV&V,” ResearchGate GmbH, June 2011
7. Sivakumar et al., “Improving Verification & Validation in the Medical Device Domain,” ResearchGate GmbH, June 27, 2011
8. “An Assessment of Space Shuttle Flight Software Development Processes,” National Academy of Sciences, 1993
9. “Compliance is the biggest risk in healthcare,” Forbes India, June 28, 2018
10. Infante, “Compliance Challenges in Healthcare: Balancing Innovation and Regulation,” March 8, 2024