Why Compliance Is Broken Today
Why do so many companies with thick binders of policies still fail audits? Or worse, suffer breaches?
The uncomfortable truth is that traditional compliance is ineffective as a consequence of its design. It relies on periodic checklists, manual attestations, and static policies that cannot keep pace with how organizations actually operate. The result is a compliance program that looks convincing on paper but fails when reality tests it.
Target was fully PCI-DSS certified when attackers exfiltrated data on tens of millions of customers. The certification created confidence in the paperwork, but it did nothing to prevent the breach. Simpson Thacher & Bartlett, one of the world’s most respected law firms, was fined £362,000 for anti–money laundering failures that persisted for years despite formal policies on the books. And Morgan Stanley paid a $15 million SEC settlement after fraudulent transactions slipped through its control environment despite written rules intended to stop such activity.
These high-profile failures underscore that even the most sophisticated organizations, with certifications and policies in place, remain exposed when compliance relies on outdated, manual approaches.
For executives, the stakes are clear. Traditional isn’t just inefficient; it’s economically unsustainable, operationally risky, and a drag on growth. Manual audits drive costs into the millions. Point-in-time checks create false confidence while exposure builds unseen. Sales cycles and product launches stall while evidence is gathered. And when customers or regulators demand proof, the organization can’t deliver it quickly.
There is another way.
Compliance-as-Code replaces the ritual of annual audits and static binders with a model that is continuous, automated, and machine-verifiable. Instead of depending on people to collect screenshots or attest to following policy, compliance is embedded directly into workflows, producing real-time evidence and continuous assurance.
Compliance-as-Code addresses multiple pressures at once, cutting costs, reducing risk, accelerating speed, and building trust by making assurance continuous, automated, and machine-verifiable.
This guide explains compliance as code in plain English for CEOs and compliance leaders: what it is, why it matters for business, and how to get started.
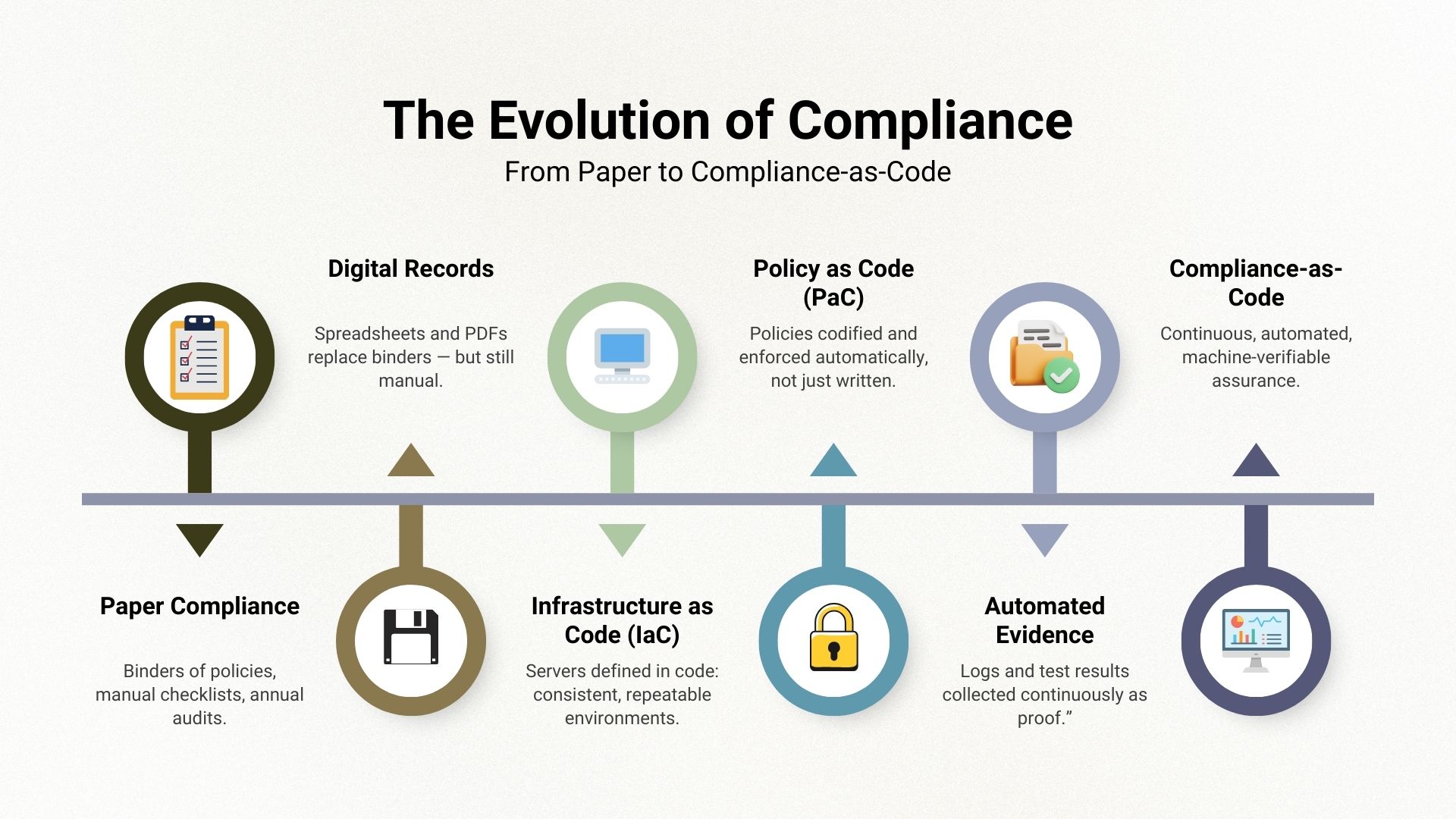
The Shift from Paper to Code
The phrase “Compliance-as-Code” can sound opaque if you’re not steeped in software culture. But the idea is simple: take something people once managed with binders and clipboards, and instead define it in a way that a computer can enforce automatically.
Think about how payroll used to work. In the past, HR clerks calculated everyone’s pay manually, double-checked against tax tables, and hoped they didn’t make mistakes. Today, payroll runs on software like ADP or Workday. Nobody wonders each month whether the system will add up paychecks correctly or withhold the right taxes — it just does. The formulas are written into code, and the code enforces the rules with machine precision, every time.
That reliability is the promise of “as code.” When a process is captured in software, outcomes are consistent, testable, and repeatable. Code doesn’t get tired, cut corners, or forget steps. It guarantees that rules are applied the same way across thousands of transactions, whether that means tax withholdings, credit card charges, or server configurations.
If payroll is the everyday example, the technology industry has been applying the same principle for decades to fix its own messy processes.
Infrastructure as Code (IaC): Traditionally, IT teams configured servers by hand, clicking through menus, adjusting settings, and installing patches one by one. The result was inconsistency: no two servers ever looked quite the same, making them hard to secure and expensive to manage. IaC fixed this by letting teams define server “recipes” in code. Run the recipe, and whether you need one server or one hundred, each is built identically. The benefit is simple: consistency, reliability, and auditability at scale.
Policy as Code (PaC): Organizational rules used to live in binders or PDFs: “passwords must expire every 90 days,” “data must be encrypted.” Enforcing them depended on people remembering and auditors checking. Policy as Code translates those rules into machine-enforceable formats. Instead of a PDF saying “encrypt data,” the system checks and enforces encryption automatically. The shift is profound: policies stop being guidance and start being guardrails.
Compliance-as-Code: Compliance is the natural next step in the broader “as code” movement. If servers and policies can be defined in code and executed automatically, why should compliance remain dependent on binders, attestations, and manual audits? Compliance as code applies the same principle to governance and regulation: the rules are expressed in a form the computer can understand, so they can be checked continuously, enforced automatically, and evidenced in real time.
In practice, this means that instead of relying on staff to collect screenshots or sign forms, systems themselves generate proof. A password policy isn’t just written in a handbook; it’s enforced directly by the identity platform. A data encryption requirement isn’t verified once a year; it’s checked automatically every time a new database is spun up. Logs and reports from these systems are aggregated into a central evidence warehouse, creating a live audit trail without additional labor.
The key shift is that compliance stops being an after-the-fact review and becomes embedded in everyday operations. Just as payroll software guarantees paychecks are calculated correctly every cycle, Compliance-as-Code ensures controls are applied correctly every time a change is made. Traditional compliance is like hiring an auditor to walk the halls with a clipboard once a year; Compliance-as-Code is like a monitoring system that works 24/7 in the background.
How Compliance-as-Code Works
To appreciate the power of Compliance-as-Code, it helps to understand its four building blocks. Think of this as the operating system that makes the business case possible:
-
Policies as Code: Instead of rules buried in PDFs, policies are written in machine-readable formats.
💡 Like moving from a Word document of spelling rules to a spellchecker that catches violations instantly.
-
Continuous Compliance: Automated checks run at the moment of change: every code push, server build, or config update.
💡 Like a seatbelt alarm: you don’t wait for your annual inspection to discover you weren’t buckled.
-
Automated Evidence: Every log, test result, or configuration snapshot is captured as audit evidence in real time.
💡 Like a security camera in a bank: continuous, time-stamped, replayable proof.
-
Integration with Existing Tools: Compliance is woven into the systems teams already use: GitHub, Jira, CI/CD, cloud providers.
💡 Like adding GPS to your car: you don’t change how you drive, you just gain guidance and assurance along the way.
Together, these mechanics turn compliance from a retrospective paper exercise into a living, automated system of assurance.
With that structure in mind, we can now examine the business impact.
The Business Case for Compliance-as-Code
The business case for Compliance-As-Code rests on three pillars: cost, risk, and speed. These combine to create trust in the business.
Cutting Costs
Traditional compliance is costly, relying on armies of people, fragmented processes, and duplicated effort that add up quickly.
Audits and compliance programs are expensive not just because of technology, but because of people. Staff time is consumed by collecting screenshots, pulling logs, and producing documents for auditors. According to a 2022 NBER working paper, “a typical U.S. establishment spends about 1.31 percent of its total wage bill on employees for performing regulatory compliance tasks” (NBER). For a firm with a $10 million payroll, that equates to $131,000 per year in direct labor; for a Fortune 500 enterprise with a $2 billion wage bill, the burden exceeds $26 million annually.
But even these figures dramatically understate the true cost of compliance. Labor captures only the visible line item. The total cost also includes:
- External audit and advisory fees, often in the six- to seven-figure range per framework.
- Duplicated effort across overlapping regimes (SOC 2, ISO 27001, HIPAA, GDPR, CMMC), where the same control must be documented multiple times.
- Delays to revenue, as new product launches or enterprise contracts stall pending audit readiness.
- Opportunity costs, with scarce engineering and security talent diverted to audit prep instead of building value.
Taken together, the total compliance bill can run far ahead of the direct labor cost. This can add up to hundreds of thousands annually for a midsize firm, and tens of millions for a global enterprise.
Compliance-as-Code attacks these costs structurally. Instead of armies of staff duplicating evidence, logs and configurations are harvested automatically from existing systems. Controls are written once and mapped across frameworks, eliminating redundancy. Evidence is continuously collected in a machine-readable format, so audit readiness becomes the steady state rather than a massive annual scramble. What once required months of human effort and multimillion-dollar budgets becomes a matter of generating a report from an evidence warehouse.
Reducing Risk
The most serious flaw of traditional compliance is that it checks narrowly, and often checks the wrong things. Audits validate controls at a single point in time, on a limited sample, and through manual, error-prone methods. A system that looks compliant in March may drift out of alignment by April. Samples chosen for testing may miss the very accounts or configurations where exposure hides. Screenshots and attestations offer surface-level comfort but don’t correspond to the real risk posture of a dynamic, cloud-driven business.
That leaves vast areas untested: infrastructure that changes after the audit, users who accumulate privileges outside the sample, configurations too numerous for auditors to review manually. The result is false confidence: certificates say “compliant” while the actual risk exposure remains untouched. This is why firms with fresh audits still make headlines for breaches and fines.
Compliance-as-Code reduces this risk by shifting from selective, retrospective checks to comprehensive, continuous assurance. Policies are expressed as code and enforced at the point of change, not months later. Automated scans test every resource, every time, rather than a narrow sample. Evidence is machine-generated and time-stamped, mapping directly to the control in question. Instead of a static snapshot, executives gain a living picture of risk posture that changes as quickly as the systems themselves.
The difference is fundamental: traditional compliance measures paperwork; Compliance-as-Code measures reality.
Accelerating Business
Traditional compliance creates bottlenecks that can stall entire projects. A vivid example comes from outside the corporate world: California’s $128 billion High-Speed Rail. Federal regulators recently found that the project was out of compliance on multiple fronts, from budget assumptions to safety testing schedules. The result has been years of delay, missed milestones, and the risk of forfeiting billions in federal funds (Axios).
The lesson here is about the cost of compliance failure. When compliance is handled through reactive reviews and static documents, gaps go undetected until they trigger costly holdups. The same dynamic plays out inside Fortune 500 companies: product launches are delayed until evidence can be assembled, enterprise sales slow while questionnaires are filled, and expansion plans stall under regulatory review. In each case, compliance operates as a brake on business momentum.
Compliance-as-Code flips this dynamic. By embedding compliance into daily workflows, evidence is generated continuously and mapped directly to regulatory requirements. Instead of waiting for periodic reviews to uncover issues, executives have real-time visibility into their compliance posture. When a new product is ready to launch, the compliance package is ready too. When a customer demands proof, it can be delivered instantly. Rather than acting as a constraint, compliance becomes invisible infrastructure that accelerates growth.
Building Trust
The cumulative effect of cutting costs, reducing risk, and accelerating business is greater than the sum of its parts: it builds trust. Customers gain confidence that controls are enforced continuously, not just certified once a year. Regulators see a posture that is transparent, consistent, and verifiable. Executives and boards gain assurance that compliance is not a liability waiting to surface, but an operating capability they can rely on.
In a competitive environment where credibility is as valuable as capital, trust is an asset. Compliance-as-Code transforms compliance from a defensive obligation into a forward-looking source of confidence that underpins growth.
With the business case established, the next step is to understand how Compliance-as-Code actually works in practice—and how organizations can embed it into their everyday workflows.
What Compliance-as-Code Looks Like Across Industries
Here’s how Compliance-as-Code plays out in real industries: what regulators expect, what controls matter, and how you implement them so assurance becomes continuous, not episodic.
Healthcare (HIPAA): Encrypt PHI Everywhere, Prove It Automatically
HIPAA governs how healthcare organizations and their partners handle protected health information (PHI), which is confidential information related to patient health. Requirements include encryption of PHI at rest and in transit, strict identity and access management, continuous audit logging, and vulnerability management. For providers, payers, and vendors serving them, failure can mean multi-million-dollar fines and the loss of critical contracts.
In practice, a healthcare platform might need to ensure that every new data store is encrypted, every access request is logged, and every privilege is reviewed. Traditional compliance would require manual screenshots and attestations; Compliance-as-Code enforces encryption automatically when a database spins up, blocks nonconforming resources, and generates evidence logs continuously.
Check out our case study, where Opsfolio helped a healthcare network centralize evidence collection and deploy continuous monitoring across systems. High-risk misconfigurations were remediated quickly, vulnerabilities triaged efficiently, and the client passed a HIPAA audit with a clean report, protecting partnerships, reputation, and growth.
Cloud SaaS (SOC 2): Change-Management Evidence Without the Scramble
SOC 2 is widely required by enterprise buyers purchasing B2B SaaS. It requires proof of secure change management, access controls, incident response, and more. For growing SaaS firms, SOC 2 certification is often a gate for contracts in banking, government, and logistics.
In a Compliance-as-Code model, GitHub pull requests, code reviews, and CI/CD pipeline runs all become machine-attested evidence. Each merge event produces a signed artifact; each vulnerability scan is logged automatically. This means the same activity that ships features also generates SOC 2 audit proof. Evidence is always current, and controls are continuously enforced.
Map Collective, a supply-chain sustainability platform, achieved SOC 2 Type I and II certification in under two months using Opsfolio CaaS. Automated evidence collection replaced spreadsheets, real-time monitoring reduced manual prep, and enterprise credibility increased immediately. The business result: faster sales cycles, improved trust, and scalable compliance operations.
Defense Industrial Base (CMMC): Continuous Assurance for Contractors
The Cybersecurity Maturity Model Certification (CMMC) sets the bar for how defense contractors protect Federal Contract Information (FCI) and Controlled Unclassified Information (CUI). CMMC requires proof of encryption, access control, configuration management, audit logging, and incident response. For contractors across the Defense Industrial Base, certification is mandatory. Without it, you can’t bid or retain DoD work.
Compliance-as-Code is a natural fit for CMMC because many of its requirements map directly to system controls. Password complexity, MFA enforcement, and session timeouts can be codified as identity policies that block noncompliant logins. Configuration baselines, such as encrypted storage or disabled insecure protocols, can be expressed as code and checked continuously whenever a server or VM is deployed. Log collection and vulnerability scans generate machine-attested evidence tied directly to NIST 800-171 controls. Instead of waiting for an assessor to sample a handful of systems once a year, Compliance-as-Code creates full coverage across every user, device, and workload, with real-time alerts when something drifts out of compliance.
Our guide to virtual desktop infrastructure enables a Compliance-as-Code approach to CMMC. By centralizing all CUI processing into a hardened enclave, contractors can enforce many CMMC controls (encryption, access, monitoring) in one place while declaring endpoints out of scope. In effect, VDI becomes a Compliance-as-Code architecture choice: guardrails and policies are encoded into the environment, enforced automatically, and evidenced continuously. It demonstrates how Compliance-as-Code principles, such as codifying rules, enforcing them in real time, and producing reusable artifacts, can reduce both risk and audit burden in the defense sector.
| Industry | Core Obligation | Compliance-as-Code Example | Business Outcome |
|---|---|---|---|
| 🏥 Healthcare | Protect PHI | Enforce encryption on every new database | Continuous PHI protection & partnerships |
| ☁️ SaaS | Secure customer data & availability | Automated security checks on every system change | Faster enterprise approvals & credibility |
| 🛡️ Defense | Safeguard CUI (DoD requirement) | MFA, encryption, and timeouts codified in policy | DoD contract eligibility & reduced scope |
How to Get Started with Implementation
The idea of Compliance-as-Code can feel abstract, but implementation is concrete and achievable. In this section, we’ll walk through the three most important practices that organizations should start with.
We’ll cover each at two levels:
- High-level explanation (executive view): Why this practice matters for business outcomes.
- Step-by-step detail: A practical outline of how a technical team would put it into action.
If you’re not technical, you can focus on the executive view and skip the details. If you are technical—or you manage a technical team—the steps show how these ideas translate into real workflows.
1. Treat Policies as Code
Why it matters: In most organizations, policies live in PDFs or Word documents. They state the rules like “all data must be encrypted,” or “passwords must meet complexity standards,” but they depend on people remembering to follow them and auditors checking after the fact. That’s slow, inconsistent, and error-prone. “Policies as code” means turning those same rules into instructions a computer can enforce automatically. This shift eliminates ambiguity, reduces manual effort, and ensures that critical requirements are applied consistently across the business.
Implementation Steps:
- Start by picking one or two high-value controls that have clear business importance, such as requiring encryption on every database or enforcing multi-factor authentication (MFA) for all administrators.
- Choose a policy engine. This is the software that reads your rules and checks whether your systems follow them. Cloud providers have built-in engines (AWS Config, Azure Policy, Google Cloud Organization Policy), and there are also independent tools (like Open Policy Agent).
- Write the rule in a machine-readable format like YAML or JSON. For example, a rule might say: “Deny any database that does not have encryption enabled.”
- Store the rule in the same system you use for other code (such as a version-controlled repository). This way, every change to the rule is tracked, reviewed, and auditable.
- Apply the policy engine to your systems so that non-compliant resources cannot be created. For example, if someone tries to create an unencrypted database, the system will automatically block it.
- Create a simple process for exceptions. If there’s a valid business reason to make an exception, it should be documented, time-limited, and tracked, with the system set to notify when it’s due to expire.
2. Build Compliance Checks into Daily Work
Why it matters: A major weakness of traditional compliance is that rules are checked only once a year, long after systems have changed. That’s like inspecting an airplane after it has already landed—it’s too late to catch problems. Compliance-as-Code fixes this by building checks into everyday workflows. Every time new code is written, new servers are created, or new changes are made, the system automatically verifies whether the change meets compliance rules. These checks, or “gates,” stop non-compliant changes before they ever reach customers, saving time and reducing risk.
Implementation Steps:
- Define what must be true before a change is accepted. For example: all code must be reviewed by another person, all tests must pass, and infrastructure changes must meet security baselines (such as encryption and logging).
- Configure your development platform so that these requirements are mandatory. In practice, this means that if a developer submits new code, the system will block it from going live until all the requirements are satisfied.
- Add automated scans that run each time a change is proposed. These scans can check for security vulnerabilities, verify that configuration rules are followed, and ensure critical policies (like MFA) are in place.
- Require approval for high-risk environments such as production. This creates an additional safeguard without slowing down day-to-day work.
- Save the results of every check as evidence. This means you automatically have a time-stamped record showing that each change was reviewed, tested, and compliant.
3. Establish Secure Baselines as Code
Why it matters: Many security incidents come from simple misconfigurations rather than hackers exploiting flaws. Examples include a cloud storage bucket left open to the public internet, a server deployed without encryption, or logging turned off by mistake. A baseline is a template that defines the minimum acceptable security settings across systems. By encoding this baseline in software, organizations ensure that every system is built securely from the start, and that any drift from the baseline is detected and corrected automatically.
Implementation Steps:
- Define your baseline. This should include rules like: all storage must be encrypted, no servers may have unrestricted public access, logging must be enabled, and only approved operating system images may be used.
- Write the baseline into code using your infrastructure automation tools (such as Terraform, CloudFormation, or Azure Resource Manager). This makes the secure configuration the default.
- Apply organization-wide guardrails through your cloud provider’s policy tools. These prevent teams from bypassing the baseline. For example, they can block the creation of a database that doesn’t meet encryption requirements.
- Set up monitoring tools that continuously check systems against the baseline. If a system drifts (say someone accidentally disables logging) the system automatically detects it and alerts your team.
- Where possible, enable auto-remediation. For example, if logging is turned off, the system can turn it back on automatically and record that action as evidence.
- Collect and store all baseline evaluation results and remediation logs in your evidence warehouse. This creates a continuous, machine-attested record that auditors can review at any time.
👉 Call to Action: Talk to Opsfolio about implementing these processes in your environment. Get Started →
The Future of Compliance-as-Code
Compliance is not getting simpler. New regulations emerge every year: from CMMC for defense contractors to HIPAA updates in healthcare to GDPR and AI governance in Europe. Organizations face an impossible challenge if they continue to rely on manual models.
Customers and regulators are moving toward a model of continuous assurance. They will expect proof that controls are operating effectively at all times, not just during annual audits.
Compliance-as-Code is poised to become the baseline. Early adopters will enjoy:
- Lower audit costs.
- Reduced legal and reputational risks.
- Faster contract closures.
- Stronger trust with stakeholders.
The laggards will struggle with ballooning compliance costs and eroding credibility.
The choice is clear: remain trapped in the annual scramble, or embrace a future of continuous, automated, business-empowering compliance.
For decades, compliance has been a necessary evil. It served as a box-checking exercise that drained resources without delivering real assurance. Compliance-as-Code offers a way out. It reframes compliance as a strategic asset: cheaper, faster, more reliable, and more trustworthy.
For CEOs, CISOs, and compliance leaders, the question is no longer whether to adopt this model, but how quickly. Those who act early will not only save money and reduce risk; they will position their organizations as trusted partners in an increasingly regulated world.
| Dimension | 📝 Manual Compliance | 🤖 Compliance-as-Code |
|---|---|---|
| 💰 Cost | Labor-intensive; armies of staff, spreadsheets | Automated evidence; costs shrink to reporting only |
| ⚠️ Risk | Point-in-time checks; narrow samples; errors | Continuous, full coverage; enforced at every change |
| ⏩ Speed | Launches and contracts delayed for audits | Always audit-ready; proofs delivered instantly |
| ✅ Trust | Certificates reassure on paper only | Real-time dashboards; machine-attested evidence |
Curious to learn more? Opsfolio CaaS helps you implement Compliance-as-Code in your environment, delivering lower costs, reduced risk, and faster audits.